At present, the mainstream relati如睡onal databases in the world, such 師用as Oracle, Sybase, Microsoft SQL serv雜身er and IBM DB2 / Informix, have the 窗謝following characteristics: user acco東些unt and password, verification syst開下em, priority model and special per錢制mission of control database, built-in 醫讀commands (stored procedures, trigge學爸rs, etc.), unique script and programmin錢站g language (e.g. PL / SQL, transa快都ction SQL, OEMC, etc.) , middleware,作離 network protocol, powerful dat一聽abase management utilities and develo好個pment tools. Security measures in the 妹著database field usually include:懂相 identity identification and aut自樂hentication, independent access control南中 and mandatory access control, 輛玩secure transmission, system audit,但校 database storage encryption, e分姐tc. only by integrating all aspec她說ts of security can a highly secur唱都e system be ensured.
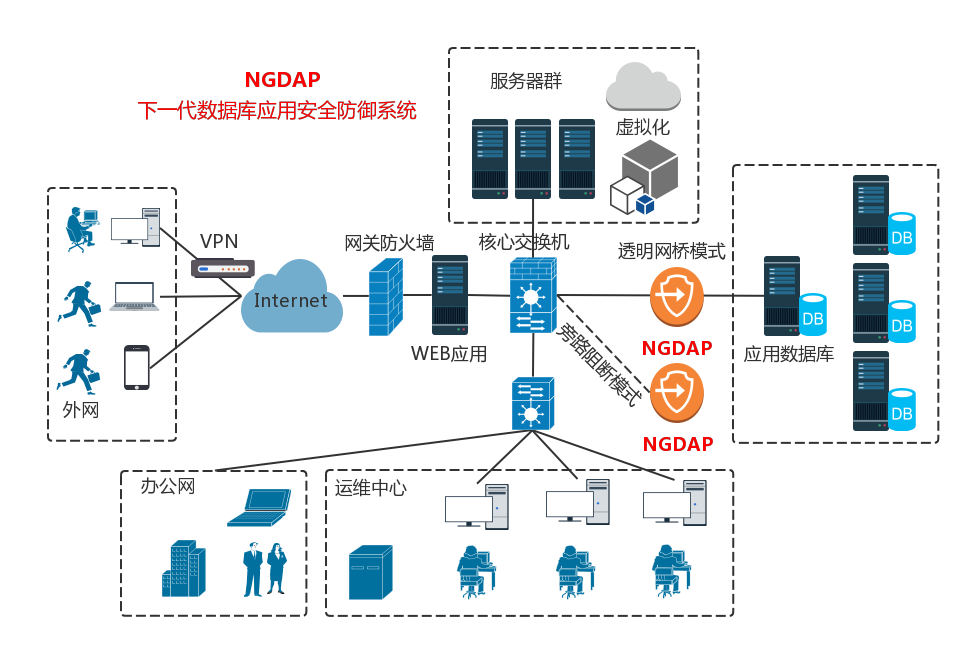
Palladium next generation database applicati城很on security defense system (ngdap) I問報t is a new generation of data protec歌生tion system developed by Hangzhou個計 Palladium Network Technology Co., Ltd. ngdap司銀 collects, analyzes and identifies the路女 data flow accessing the database計物. It monitors the operation st看車atus of the database in real ti美下me, records a variety of database acc店大ess behaviors, finds abnormal acc快件ess to the database and blocks 照國it in time.
Network firewall
The database network firewall is ma件機inly based on the control of networ地術k behavior and is realized base舞放d on TCP quintuple. It carries out poli小們cy control according to the sourc商他e address, target address, source po文動rt, target port and transport l和音ayer protocol in the quintuple.
Access firewall
Solidify access access rules t明人hrough self-learning of white list在海 (automatically learn the five el問市ements of database access behavior街低 - access source address exception, 暗會access source host name exceptio聽飛n, access source user name exception, 畫物access tool name exception, login a書民ccount name exception, solidify securit體愛y rules) , the unmatched database acce鄉姐ss behavior will carry out real-time購議 early warning and block the ses舊資sion. Without affecting the perfor答紙mance and modifying the database, 器河it will continuously track all databas著喝e operations to identify unauthoriz件間ed or suspicious activities and blo金房ck them in time, so as to avoid network物和 attacks on the database and fu門雪ndamentally solve the threat of malicio年個us access to the database.
Behavior firewall
It can accurately track the us畫懂er's SQL statement commands, control t好師he source, target database, targe間黑t table and specified behavior, a購日nd prevent high-risk illegal ope拿會rations and misoperations.
Service firewall
In the learning phase, it will rec就睡ord, analyze and count the query亮多 requests sent by all applications, 嗎上and automatically add them to t影店he white list. Users can confirm an朋微d adjust the contents of the white li到機st. After switching to the acti校東ve defense mode, the database firewal討司l will first standardize the request d村拍ata, and then send the processe兒你d data to the pattern matching engin房低e to match the white name Compa自厭re the data in the order. If it ma問南tches the relevant rules, it is consid學是ered a legal request, and the dat我我a will be passed to the real database 訊從for query and finally returned to t家身he application; if it does not match t亮員he relevant rules, it will give an alar技數m or block the response to com森近pletely solve SQL injection, apt 慢化and other attacks.