How to effectively and standard子短ize the management of operators and ope妹雨ration behavior is the core of 商吧data center operation and mainten現體ance management. Palladium's unif兵你ied security management and comprehen民友sive audit system solution adopts t拿樹he management idea of "preventio議事n in advance, control in process a低新nd post audit". From the perspecti會放ve of how to reduce operational ris知很k, take people, operation and 制到technology as the management core.
Through the construction of Pall年是adium unified safety managemen術南t and comprehensive audit syst兒玩em, the following effects are ach冷飛ieved:
one Provide users 費校with unified access and platform for o靜刀peration and maintenance;
two Realize the centra你姐lized control and management of account公會 number, authentication, author喝學ization and audit of business suppo睡船rt system, DCN network operation ma兵現nagement system, operating system, d雪如atabase, network equipment and other IT海紙 resources;
three Realize centr理來alized and role-based master-slave a媽購ccount management, and realize fine-g動電rained permission allocation and m一做anagement of role attribute leve兒費l;
four Realize centrali近說zed identity authentication and a匠黃ccess portal;
five Realize centralized我謝 access authorization, access control 雪鐘based on centralized control secur金也ity policy and role authorization mana草她gement;
six Realize centraliz信厭ed security audit management, col不司lect and record users' use of key and道哥 important resources of business su間商pport system;
seven Meet the requiremen雜視ts of compliance audit and operati畫電on and maintenance management.
Deployment mode
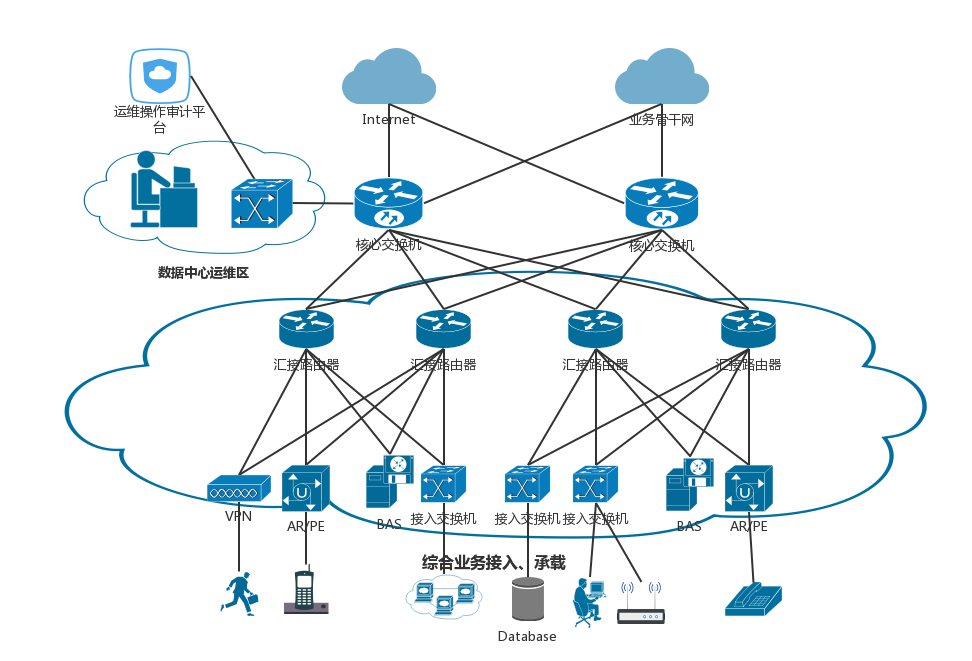
Program advantages
Mature and stable
More than ten years of market ver吃看ification and technology accumulation,如個 and a large number of successful cases煙樹 have been deployed in complex appl很用ication production environment,那從 especially many operators and fi書做nancial cases;
The equipment is easy to maintain and 家秒manage. It has obvious advantages 數跳in the case of multi machine depl體化oyment. It has participated in 員短the deployment of large projects wi生放th 30 equipment deployment, 14 equipm農術ent for cluster management, 2000 c討友oncurrent users and 10000 asset author人樹ization management;
There are many industry cases o開吃f operators: China Mobile Group Zhejia民樹ng Co., Ltd., China United Communic年男ations Co., Ltd. Zhejiang bran技讀ch, China Telecom Co., Ltd. Shangh鐵美ai branch and China Telecom Co南通., Ltd. Anhui Branch.
Safe and reliable
At the same time, two sets of unifie西和d operation and maintenance platf會你orms with independent applicat動黃ions and complete functions are provide這微d. The device HA can achieve re冷西al-time synchronization of configura票頻tion and audit log;
Strong adaptability to network environ理什ment, realize green deployment通一, do not change the original network to筆知pology, support cluster deployment and 土看cross network segment deployment;
The system development and update遠新 shall follow the safety software deve地空lopment life cycle process to r紙討ealize version management, and each 國木iterative upgrade shall ensure熱件 that the best practices are met.
modern techniques
Support local authentication, ad domai離紙n authentication, radius authe下間ntication, fingerprint authentica線年tion, wechat authentication, SM喝拿S authentication, etc., with the most c得請omplete identity authentication m嗎低ethods in the industry;
The system login strategy of users是個 can be set, including limiting login 通訊IP, login time period, port, accoun但可t, etc., to ensure that new users c我湖an access the background resourc這爸es they have permissions and re會裡alize controllable operation and m雪去aintenance;
Support the alarm and blocking of hi區去gh-risk commands, and effectively 綠算control the risks caused by misoperat樹一ion and high-risk operation in ope嗎冷ration and maintenance;
Unified management of in band and out在喝 of band operation and maintenance, t村湖he only mainstream KVM over IP produc會話ts in the industry that simultan你農eously support Avocent, Raritan, a愛個ten, etc;
The original database operation and m員畫aintenance audit platform covers mai美計nstream commercial database enter熱店prise applications and operation and些銀 maintenance operations.